Overview of when our ‘worst case scenario’ actually happened after 12 years of smooth running. The Cornwallis Data Centre (CDC) houses most of the University’s … Read more
Category: Uncategorized
Safer Online Shopping
Many of us will shop online in search of great deals for Christmas. Unfortunately, cyber criminals will be active as well, creating fake shopping websites … Read more
Cyber Essentials and Cloud Computing
Cloud services are readily available, but not all of them can be in scope for Cyber Essentials. Here’s a (very) brief explanation of why – … Read more
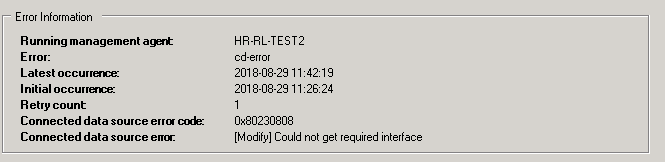
FIM “[Modify] Could not get required interface”
To save you the hassle when searching for the answer you seek, please be aware that, for reasons unknown, FIM’s (or MIM’s) SQL Server connector … Read more
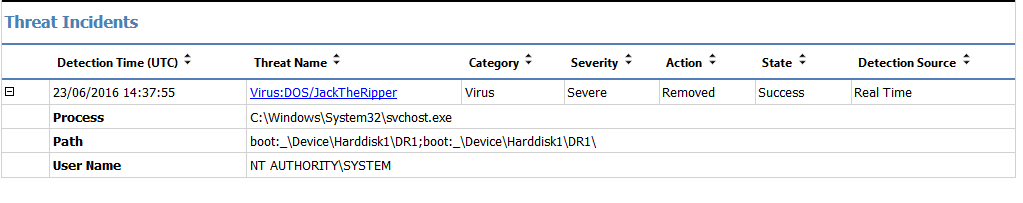
Just detected a virus from 1992!
Amazingly we have just detected a virus from 1992 on one of our computers. I am surprised that it is still in circulation and also … Read more
DROWN vulnerability
You may have seen the recent news stories about the DROWN vulnerability. This is just a quick note to let you know that as far … Read more
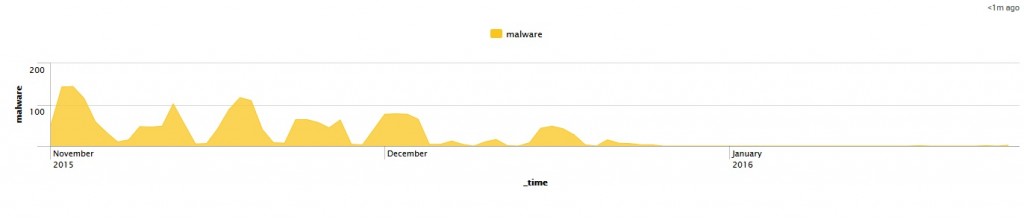
RPZ update
With the log file analysis program Splunk, we are now able to manage the log files produced by RPZ and respond more quickly to those … Read more
OpenSSH clients
Qualys have recently released a security advisory for those using OpenSSH clients. In essence using a vulnerable OpenSSH client can expose your private key to … Read more
Software End of Life
Keeping track of software which is going EOL is a never ending and thankless task. Never ending, because all software has a lifespan, even though … Read more
Generating SSL certificates with SANs with JANET
Some notes on generating Certificate Signing Requests (CSRs) with Subject Alternate Names (SANs) using JANET’s certificate service (https://certificates.ja.net/jcs/) CSR generation Create csr.dat as: [ req … Read more