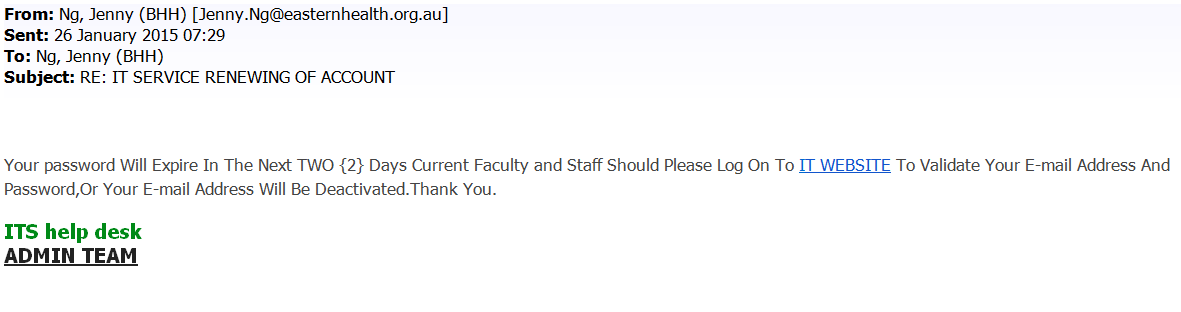
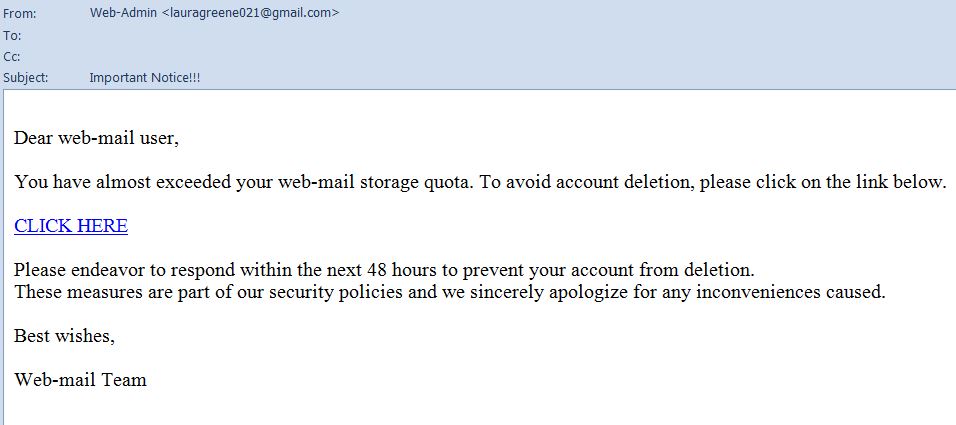
The University makes every effort to screen out mischievous and malicious emails but inevitably these find their way to our inboxes. While many are crude and easy to delete with a clear conscience, others exploit that we are busy and imply that unless corrective action is taken we might lose email access or network access, for example, as the following examples do.
It should be fairly obvious from the sender details that these do not originate from within the University. Kent passwords generally only have to be changed about once every 9 months and when that date is looming you will receive one or more reminders from Information Services, beginning about 4 weeks before the date the password expires.
Even if you were to miss this and allow your password to expire it is quick and easy to have it reset (and definitely far less trouble than a potential breach of privacy could lead to).
If you are genuinely near your email storage quota this will be flagged up in your email client (Outlook or OWA in most cases) and a notification from IS (rather than from a gmail address or similar) will give instructions.
It is likely that in both the examples shown the links will lead to a spurious website that asks you to enter old and new passwords, and possibly other information. If you use the same password (either old or new) for other websites this will put you at risk. It will certainly make it quite likely that your Kent email account becomes compromised.
IS advice: http://blogs.kent.ac.uk/isnews/how-to-spot-fake-emails/
If you have clicked on a link in an email of this kind, and then entered password change details, you are strongly advised to change your Kent password again (and any other passwords that might match either of the “old” or “new” values you entered). https://account.kent.ac.uk/changepassword/
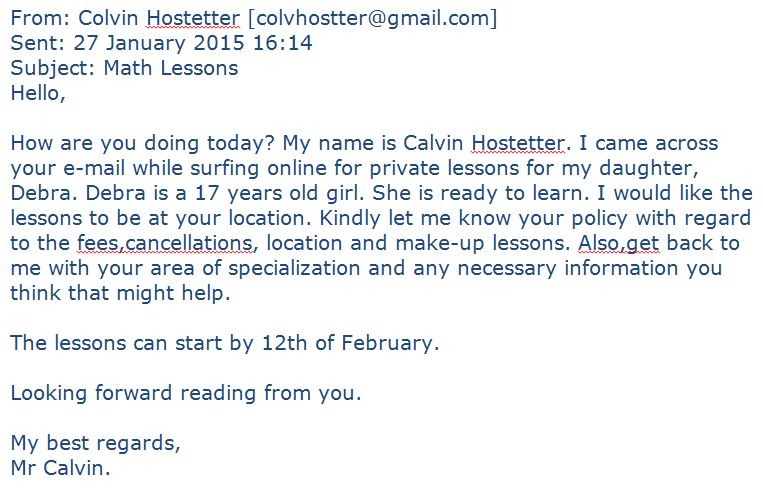
Here is another, perhaps more subtle, variation. This time the aim of the exercise is to try and scam the recipient by appealing to their wish to maybe supplement their earnings…
While the style of English may sound faint alarm bells, the fact that this is from an unknown email address may not because it is plausible that a stranger might find contact email details on the web – via the SMSAS People pages for example. The differences in the name “Calvin” given initially a forename but lower down as though it were a family name is odd (and it is spelled “Colvin” in the “From” field)… but even so there’s no links that might be malicious and what harm could it do to reply?
Scams like this can work as follows:
- I reply to the email and cite some figure as my charge per hour, plus other particulars.
- Calvin/Colvin or maybe even Debra reply and say “…that’s great, perfect, let us send you a bank draft straight away”.
- What seems to be a payment arrives but it’s massively more than might have been expected. For example the scammer said they’d send you a £100 payment in advance but the payment seems to be for £1000.
- A little while later an apologetic message arrives saying that they made an error but wouldn’t it be easiest if you kept the payment and refunded them the over-payment?
And the rest you can guess! A variant on step 2 would be to request sort code and bank account so that they can send you the funds….
See this blog entry for an uncannily similar attempt: http://sites.udel.edu/threat/2014/10/08/lessons-con/