Response Policy Zones (RPZ) can be used not only to protect the University community from botnet command and control traffic, but also connections to malware domains.
If unprotected your computer could be at risk of such activities as phishing (where a fraudulent web site trick you into handing over your private details), downloading additional malware, malware infected adverts and the like.
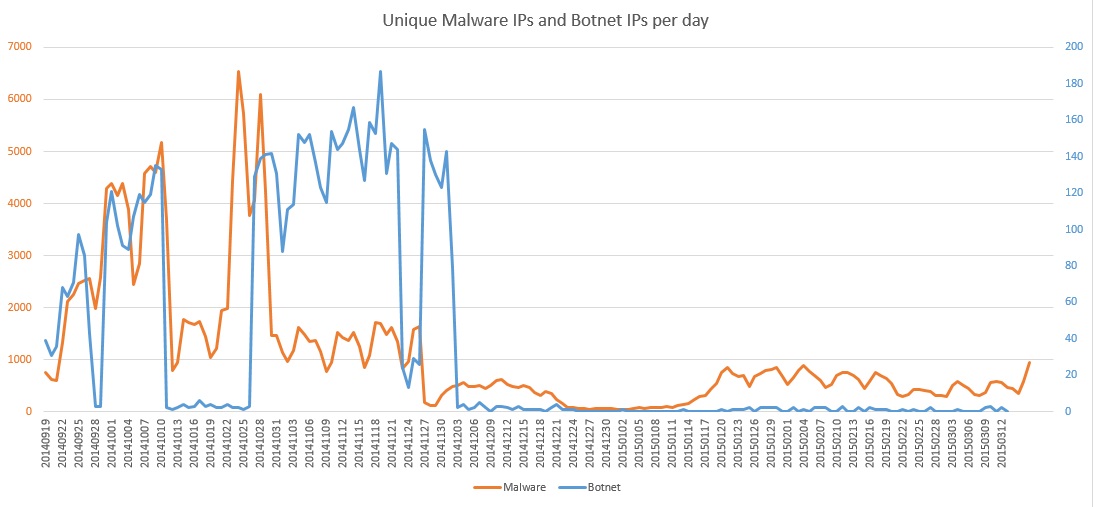
Below is a graph with the connections from individual IP addresses to these malware domains, with the botnet C&C traffic shown on the same timeline – this runs from Sept 2014 to mid March 2015. The botnet traffic is shown in blue and uses the y-axis on the right. The malware traffic is shown in orange and uses the y-axis on the left.
It is important to note that these are not a count of the infected devices on the network. Each user may have a number of different IP addresses during the day due to the way in which we manage the address space on the eduroam wireless.
Whilst the graph shows a reduction in the numbers of malware, we have not yet been able to reduce it to the levels of botnet C&C traffic. This is something we hope to address as many of the people using these devices will become BYOD users of the future and connect their devices to other networks.
Also of note is the increase in mid-late Jan 2015 which coincides with the start of term.
It will be interesting to monitor these numbers and see what happens when the new academic year starts and approximately one third of our student cohort turns over.