We’ve been testing Response Policy Zones (RPZ) aka DNS firewalling since June last year to see if we could measure the amount of traffic to botnet command and control servers and malware domains from our network since June 2014.
A botnet is a collection of computers (and the numbers range from a few hundred to millions) which have been taken over by a bot herder. The bot herder sends commands out to the bots in order to use their compute power and / or bandwidth for nefarious purposes. This could be spewing spam, sending connection requests to a specific server – causing a denial of service attack, or anything the bot herder wishes to do with the computers under his control.
Whilst the diagram below shows a botnet, the reality is that these are dynamic collections with computers constantly being added and removed as people get infected and clear them up.
Initially RPZ was set to logging mode only, so we could see the attempts to connect to these command and control servers without actually blocking them. This allowed us to see that there would be no untoward impact on the servers where it runs.
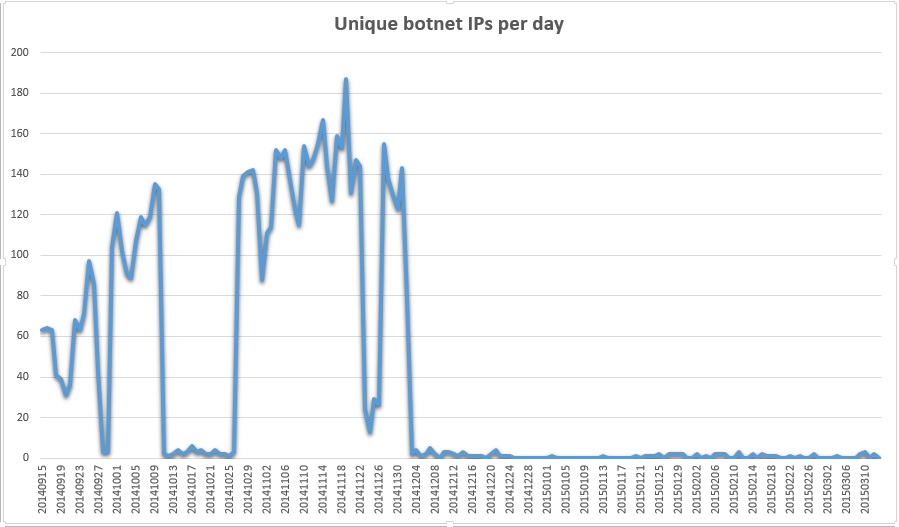
In late summer 2014 we switched on the blocking of connections and this is the graph of results:
We don’t know what caused the sudden drop in October 2014. There are a number of theories but we cannot say for sure:
- Botnet take down. Some Law Enforcement action may have disconnected a number of command and control servers, causing the botnets to go quiet
- Infected computers were taken on off site. We suspect that there is a reasonably small number of infected computers generating the hits shown on the graph. If they were off site for 2 weeks, then the traffic would drop
- Antivirus software detected the malware. It may be that as malware samples were shared amongst the antivirus software companies, the malware was removed or so disabled that it took the bot herders some time to re-infect computers or re-activate their malware
- The bot herders may have ordered their botnet to go quiet for some reason
The only thing we can say with certainty is that there was a concerted effort from the helpdesk to identify and cut off the accounts of those running infected computers. The accounts were re-enabled when a clean antivirus scan result was shown.
With the amount of botnet command and control traffic under control and down to an irreducible minimum, the focus can now shift to identifying computers connecting to malware domains. Watch this space.
If you have any questions, please post them in the comments