Final year Undergraduate student Oliver Florence explores deception detection and a new technology being developed at The University of Kent’s School of Computing.
Although the idea of being strapped into a polygraph machine might well make you uncomfortable, it seems as though there isn’t much to be worried about.
The American Psychological Association assert that ‘Most psychologists agree that there is little evidence that polygraph tests can accurately detect lies.’ But even though the consensus seems to be that they don’t work, they are still being used by the police, and in the workplace.
Given that they don’t work, why are they still used? The answer is perhaps a combination of two factors. People are not aware of how inaccurate polygraphs are, and there are numerous studies showing that the effect of being plugged in to these all-knowing machines makes people more likely to tell the truth, or at the very least offer up more information than they would, were they not covered in measurement equipment. This is referred to as the bogus pipeline effect.
Polygraphs are not the only technology available that make the claim of being able to detect deception though. There are a number of other technologies used for lie detection that all have various criticisms laid upon them. The common theme of the criticisms is that the person being tested is able to consciously modulate their physiological responses to the stimuli and make the technology give inaccurate results. Differing methods of response measurement tend not to produce notably different success rates, and as a result it seems that we’re still left without lie detection technology that is accurate enough for us to say ‘it works’. Or are we?
A research team led by Professor Howard Bowman at the University of Kent have created a technology called the Fringe-P3 method. Howard Bowman holds two part-EEGtime positions, one at Kent as a Computer Science professor and the other at Birmingham as a Psychology professor. Having spent the first phase of his academic career on developing mathematical theories of computation, Professor Bowman now focuses entirely on the field of Cognitive Neuroscience.
The Fringe-P3 technology is able to circumvent the traditional problem deception detection machines have faced; it presents the stimuli to the subject in a way that means they are unable to employ countermeasures.
A simplified yet useful means of describing the technology is to split its description into two parts. Firstly the way the subject’s response is measured is with Electroencephalography (EEG), which is used to measure a brainwave called the P3. The second and more important aspect is the way the stimuli are presented to the person. This is done with rapid serial visual presentation (RSVP), which in this case means presenting the person a series of stimuli very quickly. So quickly in fact, that the subjects are able to recall very few of the stimuli presented.
The result of this RSVP is that the subject is unable to attempt to fool the measurement device, as they aren’t aware of some key stimuli that have been presented to them. According to Bowman this is a result of the stimulus being on the ‘fringe of awareness’, meaning that the brain will unconsciously process the stimuli until it is presented with something that causes perceptual breakthrough. Perceptual breakthrough is the transition of information from your unconscious to your conscious mind, or in simpler terms, the act of conscious recognition.
This method of deception detection is described by Bowman as ‘piggy backing’, as the EEG measurement in isolation is just whether or not the person has consciously recognised the stimuli. It’s the context and content of the stimuli coupled with the detection of conscious recognition of stimuli that indicates whether or not the person is attempting deception. An example of how deception can be detected using this technology is asking a subject if they have ever met a specific person, and then showing them the person’s face using RSVP. If the subject claims to not know of this person but exhibit a large P3 when tested, you can know that they’re not being truthful.
The experiments carried out by Bowman and his team have demonstrated the effectiveness of the Fringe-P3 technology. Subjects were given a ‘fake name’ to pretend was theirs and then shown a series of names using RSVP.
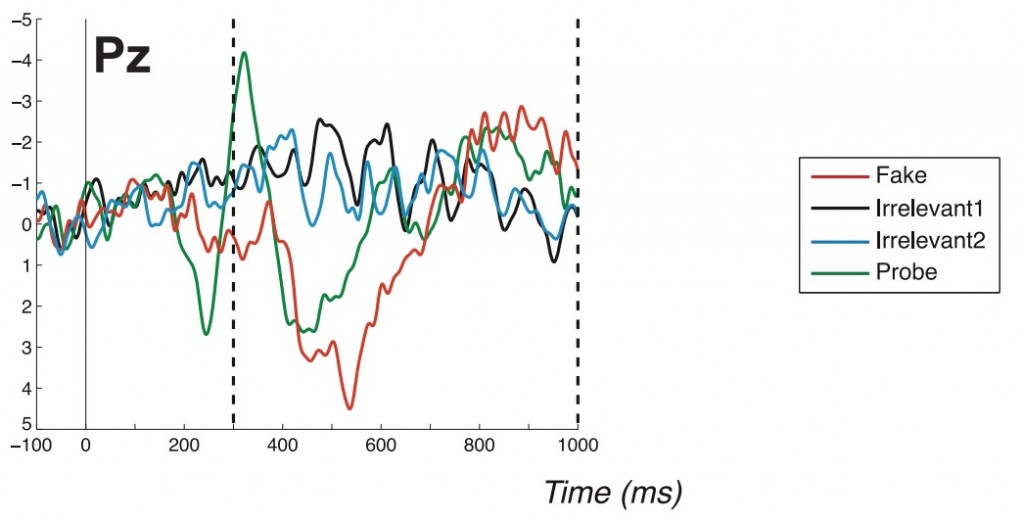
The graph below shows the averaged data for the experiment carried out in Bowman’s paper. The two dotted lines on the graph represent the area in which you would expect to see a modulation in the P3 wave when a subject is presented with something they consciously recognise (in this case their own name).
‘Probe’ represents the subject’s real name, ‘Fake’ represents their assumed name, and irrelevant were two names unknown to the subjects. – A convention of this type of graph is that the Y axis is upside down, so in this case the downward spikes indicate positive deflections.
When the subjects were shown their own names (probe) and their assumed names (fake) a spike was produced in P3 modulation clearly showing the subjects perception of the stimuli. The difference between the irrelevant P3’s and the probe/fake is the evidence that perceptual breakthrough has occurred.
The knowledge one can potentially acquire by using the Fringe-P3 method is better suited to indicating innocence as opposed to proving guilt. The example given earlier of a subject claiming not to know someone that they are shown to consciously recognise could have use in the real world, but this only indicates that they recognise them, not that they have committed a crime.
There have been numerous alleged cases of fabricated amnesia. These allegations have traditionally been very difficult to prove. The use of the Fringe-P3 technology could aid in the diagnosing genuine amnesia by demonstrating the absence of conscious recognition on a neurological level.
The creation of this technology by Bowman and his team is a significant move forwards in the way deception detection is approached. Its effectiveness has been demonstrated in a number of contexts all of which benefit directly from its ability to resist countermeasures. According to Bowman’s team there are still many unexplored possibilities and benefits that require further experimentation, so for the moment at least, this lie detector will stay in the hands of its creators.