Are BT really asking us to switch off Trusteer Rapport protection for some websites?
The filters introduced by UK ISPs in response to Cameron’s request for porn filters have the internet buzzing with speculation and problems identified. Although experts had identified the problem already in the last century, this week even BBC’s Newsnight found out about overblocking (including, but not limited to false positives).
The BT service’s help pages are very useful in trying to find out what is really going on. Last night I stumbled upon a very interesting one indeed, called “I can’t access a number of websites that I’ve protected with the Trusteer application“. Relevant for me as my internet banking provider has provided me with Trusteer Rapport for protection. [I have considered the risks of disclosing that I use internet banking – yes I’m now a slightly more likely target, and security experts will possibly find me foolish for using it at all. So be it.]
The help page mentions as a symptom “You may receive a ‘You have tried to access a non-BT DNS server’ message when blocking with the Trusteer application.” I read this as: Trusteer redirects protected DNS requests [i.e. translating the wordy URL like blogs.kent.ac.uk into the numerical IP address of the server it represents] to its own DNS server instead of BT’s one. This is presumably done as a part of the protection package in order to prevent one particular kind of attack called “DNS hijacking”. However, this doesn’t work with BT filters because they operate at the level of the DNS server (likely given the main business of the third party provider, Nominum, that BT use for filtering, is indeed DNS servers, according to their webpage).
So what’s the solution? The help page says “You’ll need to remove or disable these manually added sites from the protected list within the Trusteer console.” That sounds a bit dubious, so we decided to protect these sites (for our internet banking or some other reason), and BT now tells us to remove this protection?
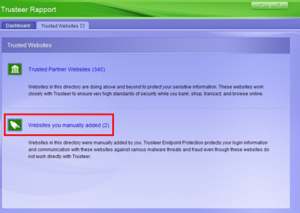
I’ve copied a helpful screen shot from this help page below. This is where you need to go in Trusteer Rapport to fix the problem. Note that there is a list of 345 “Trusted Partner Websites” which have a closer link with Trusteer (not with BT).
So my current best guess is that my bank is one of those 345 trusted organisations. The BT filters presumably load this list from Trusteer, and if they see a DNS request for one of these web pages redirected they’ll accept it – but not if it is a redirected DNS request for a site that you’ve manually added to Trusteer for protection.
Thus, it is likely that nobody’s internet banking has lost any protection yet, because banks would likely get themselves on the trusted organisations list before rolling out Trusteer Rapport to their customers. Relying on the customers configuring Trusteer Rapport themselves by manually adding the bank’s website adds another possible failure point. This is in a context where banks are drawing back from covering all losses incurred through internet banking crime. (Only the other day my colleage David Chadwick was on regional TV commenting on a case where NatWest had refused to cover a 20k internet banking crime loss because the recommended software hadn’t been installed by the customer.) Trusteer Rapport suggests to add this kind of protection to any web connection that carries sensitive data, but broad use of that functionality thus appears incompatible with the BT’s filters.
When I first spotted this I raised it through Twitter @btcare immediately. No reply yet.
Disclaimer: I have only basic rather than expert knowledge of DNS and hijacking, spoofing, etc. Maybe there’s a simple answer somewhere still.
Update: Duh. Is this a crude fix for an obvious way of circumventing the filter (install Trusteer Rapport and protect the website you want to visit)? Sounds like with the error message and with the help page BT have given away too much information.
Related posts: You can read my speculation about what will happen next in terms of internet censorship in “Anonymity will be the next victim of internet censorship“.
Earlier comments on using internet censorship to combat extremism are in
Blocking extremist sites is not the same as fighting child porn.