With the log file analysis program Splunk, we are now able to manage the log files produced by RPZ and respond more quickly to those computers which we see trying to contact known malware domains and botnet command and control servers.
This, combined with a trial of the Suricata Intrusion Detection System whose log files are also analysed with Splunk, has allowed us to make a significant and lasting reduction in the amount of malware seen on the University network (staff, students, and visitors):
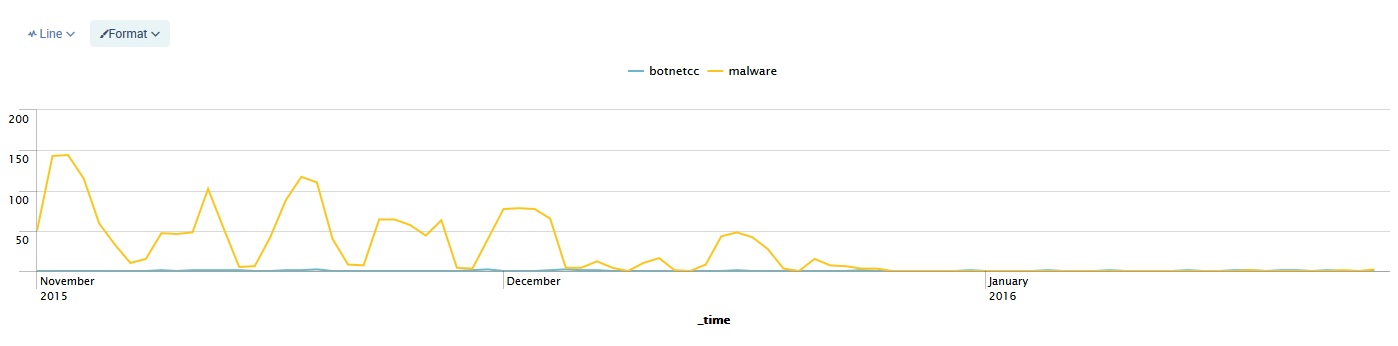
This graph shows the number of both malware and botnet command and control server hits per day from the RPZ logs since November 1 2015:
January 2015’s uptick in events around the start of term was not repeated in January 2016.
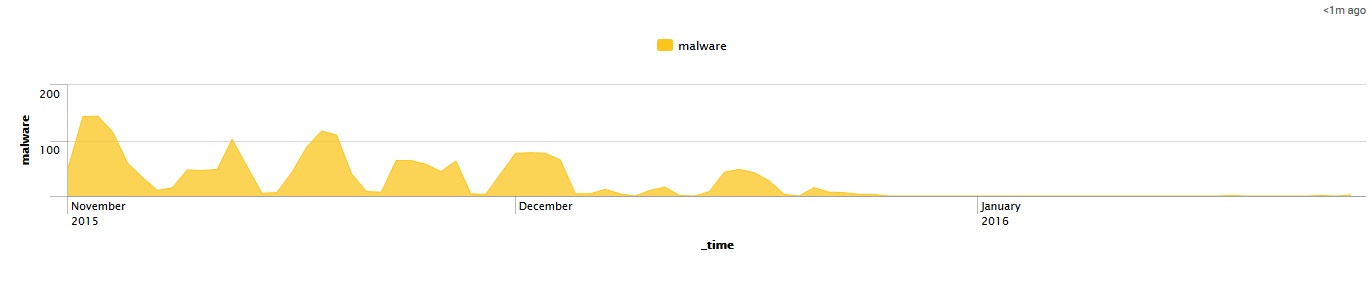
This graph shows the number of malware server hits per day from the RPZ logs since November 1 2015:
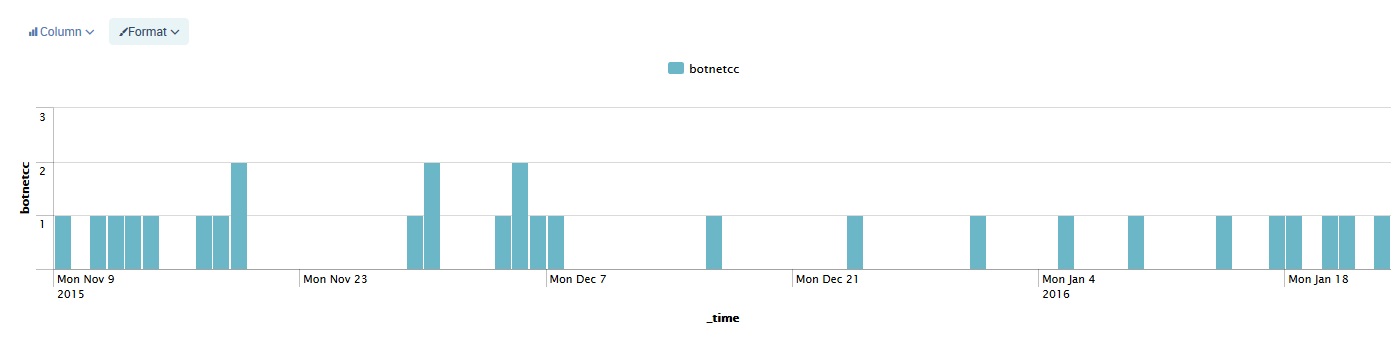
 This graph shows the number of botnet command and control server hits per day from the RPZ logs since November 1 2015:
This graph shows the number of botnet command and control server hits per day from the RPZ logs since November 1 2015:
 Thanks go to the Server Infrastructure Team for their help trialling Splunk and Suricata, and to the Helpdesk for their efforts in identifying users from the reports and getting them to scan their computers (and phones) to remove malware.
Thanks go to the Server Infrastructure Team for their help trialling Splunk and Suricata, and to the Helpdesk for their efforts in identifying users from the reports and getting them to scan their computers (and phones) to remove malware.